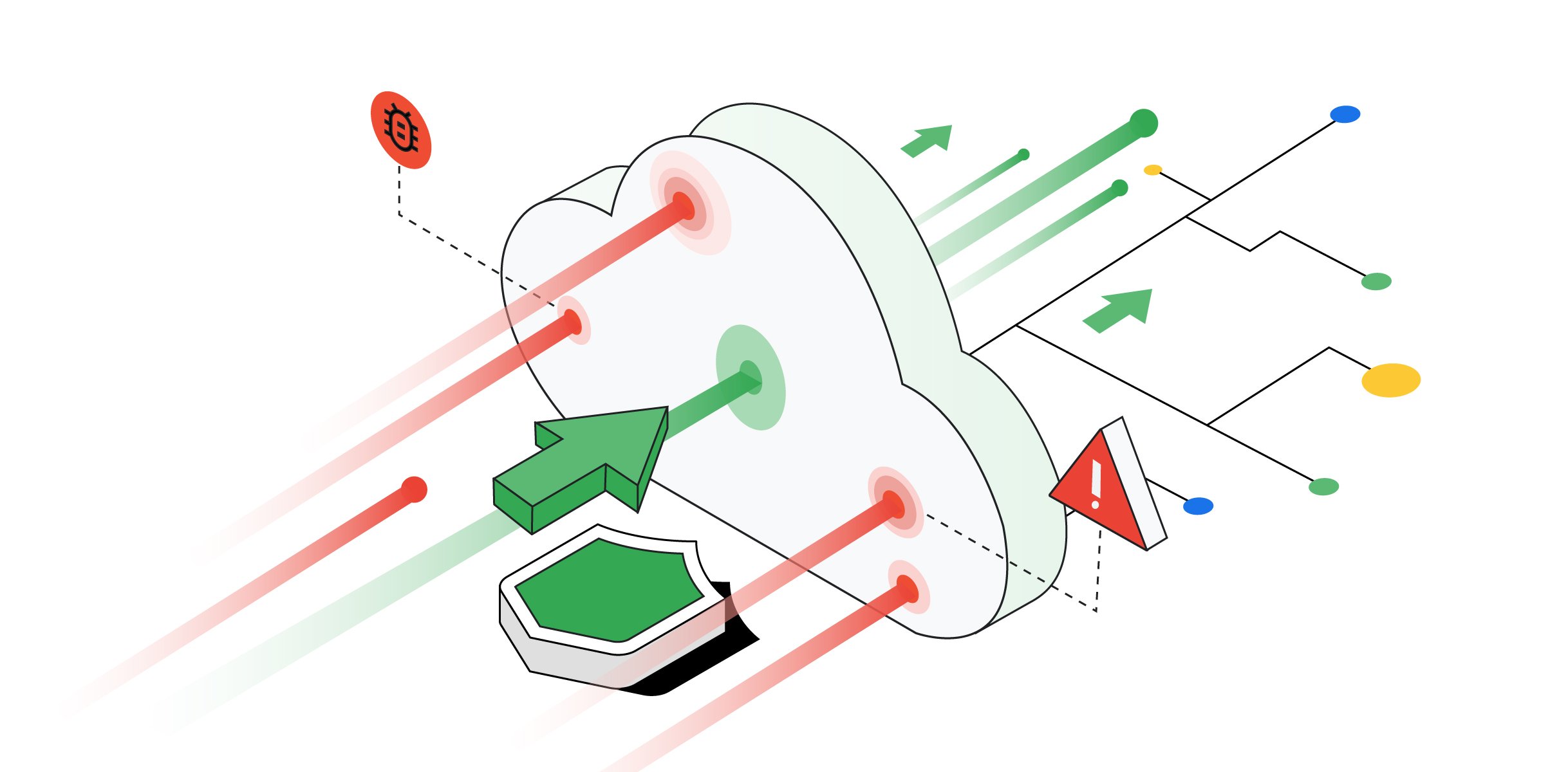
In the ever-evolving landscape of cybersecurity, Distributed Denial of Service (DDoS) attacks have become a pervasive threat. Recently, Google found itself at the forefront of a monumental challenge, mitigating the largest DDoS attack recorded, with a staggering peak above 398 million requests per second (RPS).
Understanding DDoS Attacks
DDoS attacks involve overwhelming a targeted online service with a flood of traffic, rendering it inaccessible to users. These attacks come in various forms, from volumetric attacks to sophisticated application-layer assaults. The impact of such attacks is profound, causing service disruptions and potential financial losses for businesses.
Google’s Encounter with a Massive DDoS Attack
In a surprising turn of events, Google faced a colossal DDoS attack that tested the limits of its infrastructure. The attack reached an unprecedented volume, peaking at over 398 million rps, highlighting the need for robust cybersecurity measures.
Importance of Mitigation in DDoS Attacks
DDoS mitigation is the key to safeguarding online platforms from such onslaughts. It involves deploying countermeasures to identify and filter malicious traffic, allowing legitimate users to access the services without disruption.
Google’s Defense Mechanisms
Google, being a tech giant, boasts a sophisticated security infrastructure. In response to the massive DDoS attack, Google swiftly implemented a series of defense mechanisms. These included traffic filtering, rate limiting, and collaboration with global cybersecurity experts.
Unraveling the Complexity of the Attack
The sheer scale of the DDoS attack on Google was not a simple feat to overcome. Several factors contributed to its complexity, including the use of botnets, multiple attack vectors, and the sheer volume of requests.
The Role of Burstiness in DDoS Attacks
Burstiness in DDoS attacks refers to the sudden and intense surges in malicious traffic. This dynamic nature poses a challenge for traditional security measures. Google’s successful mitigation of the attack underscores the importance of addressing burstiness in cybersecurity strategies.
Perplexity in Cybersecurity
Perplexity, or the unpredictability of cyber threats, adds another layer of complexity to security measures. In the case of the Google DDoS attack, the perplexing nature of the assault posed a formidable challenge during the mitigation process.
Specifics of the Google DDoS Attack
The targets of the attack included various Google services, leading to disruptions in access for users worldwide. The attack persisted for a significant duration, requiring Google’s cybersecurity teams to work tirelessly to restore normalcy.
Lessons Learned from the Incident
Post-incident analysis by Google revealed valuable insights. Changes and improvements in security protocols were promptly implemented, emphasizing the continuous learning and adaptation required in the face of evolving cyber threats.
The Growing Threat Landscape
The incident at Google reflects broader trends in the escalating scale and sophistication of DDoS attacks. Organizations must stay vigilant and continuously update their security measures to counter emerging threats effectively.
Securing the Digital Future
Addressing the growing threat landscape necessitates collaborative efforts within the cybersecurity community. Innovations in DDoS prevention technology, threat intelligence sharing, and coordinated response strategies are crucial for securing the digital future.
Engaging the Reader with Real-world Examples
To put the severity of DDoS attacks into perspective, consider past instances where major online services faced similar challenges. These real-world examples help readers grasp the significance of robust cybersecurity measures.
DDoS Protection for Businesses and Individuals
The Google incident serves as a reminder for businesses and individuals alike to prioritize DDoS protection. Implementing security measures, such as firewalls, intrusion detection systems, and DDoS mitigation services, is essential for safeguarding online presence and data.
Conclusion
In conclusion, Google’s successful mitigation of the largest DDoS attack to date underscores the importance of proactive cybersecurity measures. The incident serves as a wake-up call for organizations and individuals to stay ahead of evolving cyber threats, fostering a secure digital environment.
Frequently Asked Questions (FAQs)
Q: How common are DDoS attacks?
A: DDoS attacks are increasingly common, with thousands occurring daily across the globe.
Q: What steps can individuals take to protect themselves from DDoS attacks?
A: Individuals should use reputable cybersecurity tools and services, such as VPNs and firewalls, to enhance their online security.
Q: How long did it take for Google to mitigate the massive DDoS attack?
A: The duration of mitigation efforts was not disclosed, but Google acted swiftly to address the attack.
Q: Can small businesses be targeted by DDoS attacks?
A: Yes, small businesses are also susceptible to DDoS attacks, and implementing security measures is crucial for their protection.
Q: What innovations can we expect in DDoS prevention technology?
A: Continued advancements in machine learning, AI, and collaborative threat intelligence sharing are expected to shape the future of DDoS prevention technology.